How cybersecurity plays a pivotal role in your financial stability
The digital age has led to ultimate convenience.
We’ve come to expect ease of use from our financial lives: Investment performance, insurance coverage, retirement balances, credit card activity, and even financial planning projections are available at your fingertips.
However, having your most personal information in the “cloud” makes it more accessible to others as well, and not everyone has good intentions. In 2021, the global cost of cybercrime exceeded $6 trillion.1
In a paper world, forms were forged, fraudulent claims were submitted, accounts were defrauded, and companies were exploited. In many ways, we are much better off now than we were 30 years ago.
The minds that invented the internet also found ways to secure it through passwords, authentication, and encryption. We have the tools needed to build a technological fortress around our personal information and finances.
Criminals today twist the benefits of digital money tools into its greatest weakness.
You are busy. You need your financial documents to be able to follow you wherever life takes you.
When you are as busy, you also may rush through things, and a failure to vet phone calls or emails could put you at risk.
The most common financial scam we see in the financial services are fraudulent wire transfers. After all, it’s not uncommon for our clients to need to wire money. Wiring money is fast and between trusted parties, very secure.
However, if a client’s email is hacked, our policies and procedures are put to the test.
A few stand out as seemingly legitimate withdrawal or wire transfer requests from existing client emails – requests ranging between $9,500 to $69,500. But, when our staff verbally verifies the request with the client, many are deemed fraudulent. No money is moved, and everyone wins—except the criminals.
Stories like these are a perfect example of what we face as we try to balance the value of both accessibility and privacy. It also goes to show that no matter how criminals seek to take advantage, people who understand and take the steps needed to protect their information will almost certainly be successful:
Table of contents
- Use strong passwords.
- Set up multi-factor authentication on any account that offers it.
- Review accounts regularly.
- Stay vigilant about email scams.
- Avoid giving out personal information over the phone.
- Align with companies that prioritize cybersecurity.
Best practices for keeping your money secure online
1. Use strong passwords.
The first line of defense for your financial accounts is a strong password.
Characteristics of a strong password include:
- A mix of lowercase and uppercase letters
- Numbers (0-9)
- Non-numerical characters (!@#$, etc.)
Additionally, passwords should not be made up of personal information that is easily linked, such as names, birthdates, or phone numbers.
Finally, avoid using the same password on multiple accounts. If a hacker successfully accesses an account with one password, they immediately begin testing that password on other accounts.
The best way to manage this large number of passwords is to use a password manager to generate and store secure passwords for your accounts.
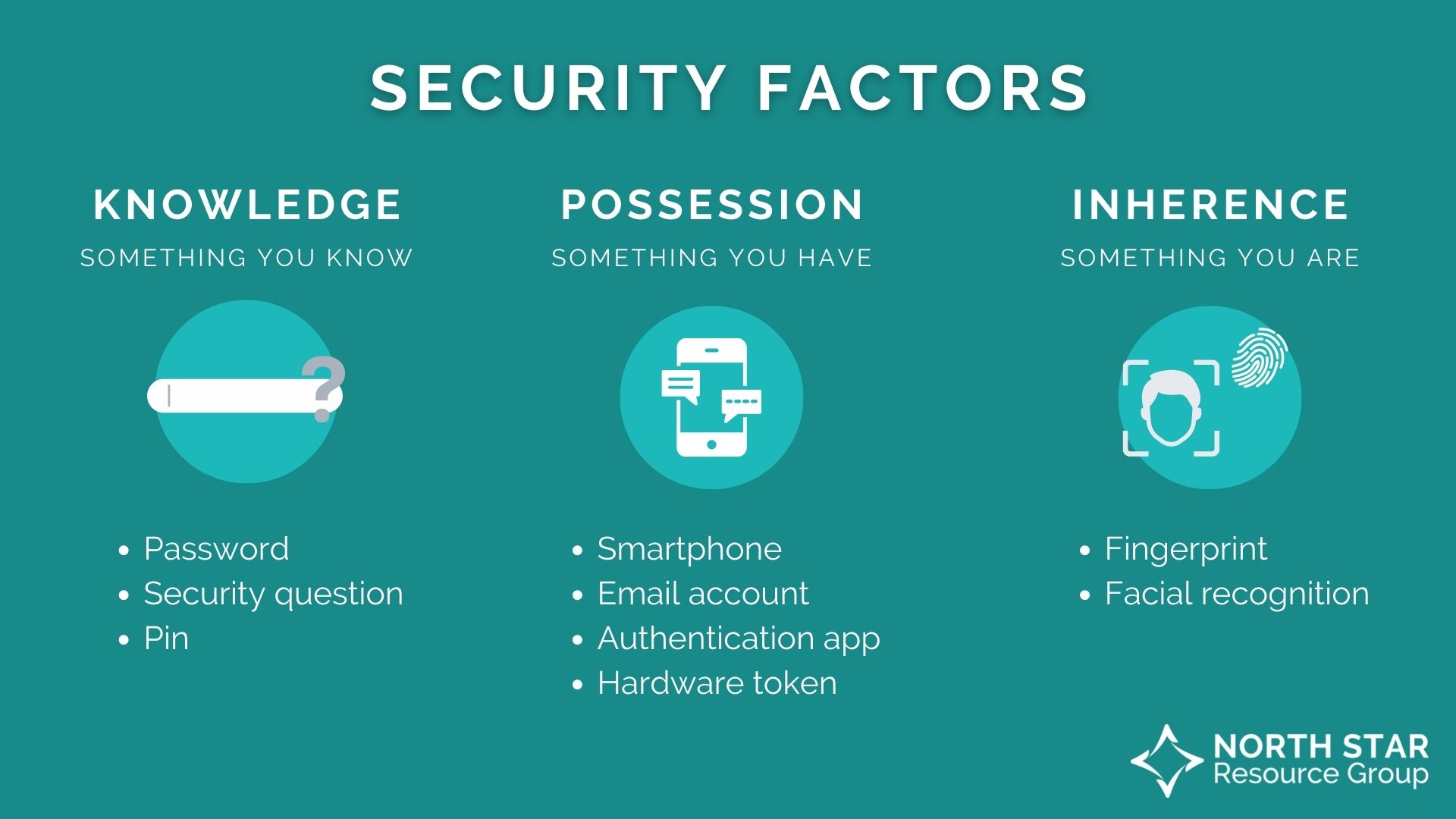
2. Set up multi-factor authentication on any account that offers it.
Multi-factor authentication (MFA) is a process in which a user must provide two or more authentication methods to gain access to an account.
MFA adds the step of verification between password and access.
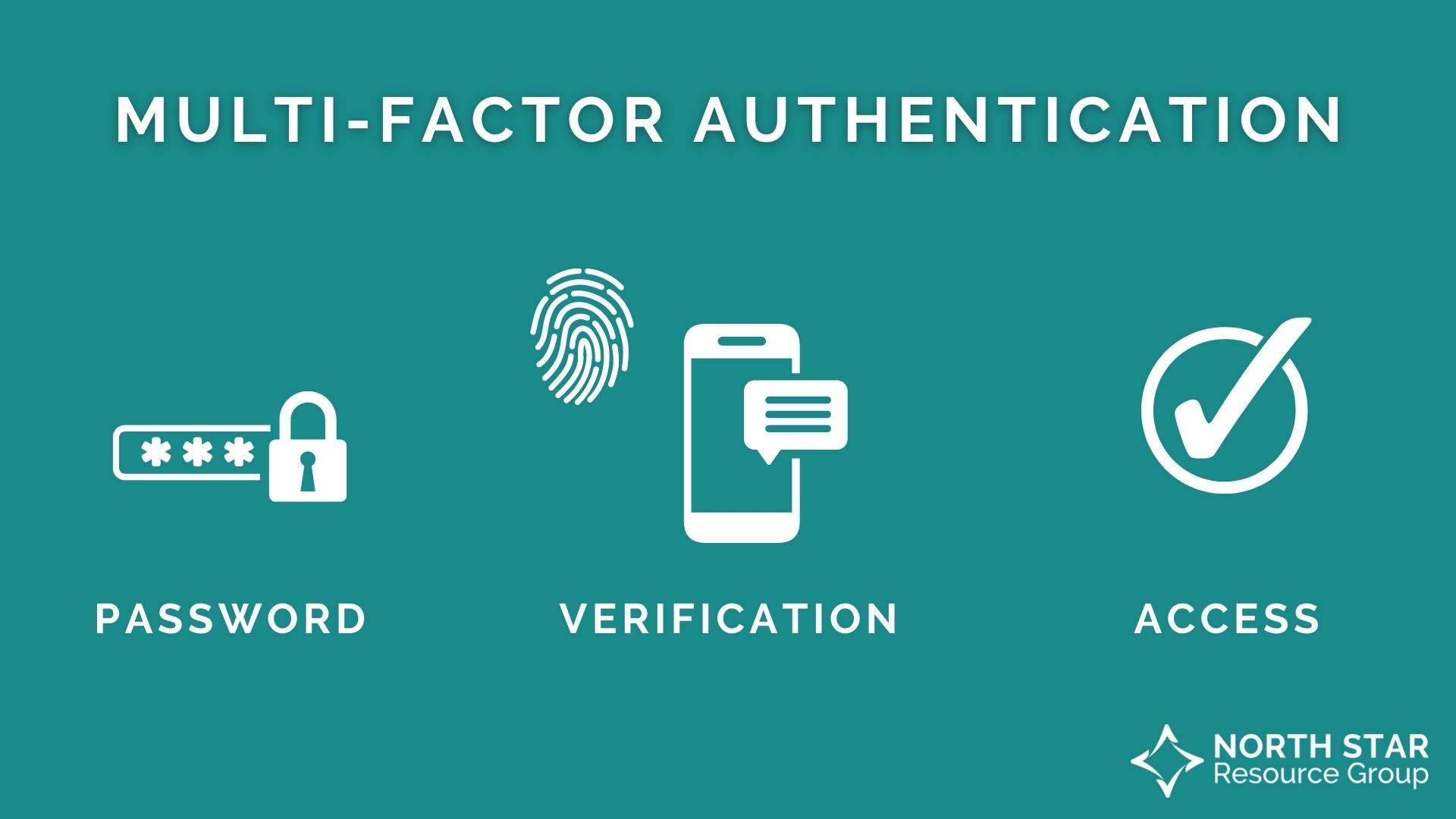
An example of this is when you attempt to log in to your email and after entering your password, you are prompted to answer a security question, or when you must use a fingerprint and an access pin when you restart your phone.
This extra layer of protection combines security factors of knowledge (something you know), possession (something you have), and inherence (something you are).
Many financial accounts and platforms require multi-factor authentication already, and it is in your best interest to ensure it’s set up with as many factors as recommended!
of account-compromising cyber-attacks can be blocked by multi-factor authentication.2
3. Review accounts regularly.
Your best form of data privacy is prevention—strong passwords and appropriate multi-factor authentication. These two measures alone can block 99.9% of account-compromising attacks in their tracks.
However, in the 0.1% chance your account is compromised, the earlier you catch the issue, the easier it will be to fix.
Keeping an eye on your investment balance and credit score can help you spot anomalies and areas of concern when they appear. Then, knowing a precise time the issue occurred can help you resolve it in a more timely and accurate manner than when you’re trying to determine if the issue occurred two days or two months ago.
Check your financial information periodically, ask for an occasional copy of your credit report, and keep an eye on your monthly statements and don’t be afraid to check in if something seems off.
Your financial professional can serve as an advocate in this regard, as someone who can field your questions about whether changes are due to the markets or malicious activity and who can help investigate issues on your behalf if needed.
4. Stay vigilant about email scams.
Email is the ultimate tool for convenience, and bad actors will occasionally take advantage of this, replicating logos and language of trusted companies and asking you to click a link or perform an action to gain access to your machine or information.
There are a few things to keep in mind to avoid any email phishing attempts:
- Check the “From” field. Make sure the email is from a sender you recognize. Often, phishing emails will come from email addresses that are misspelled or unrelated to the company they are spoofing.
- Hover over links. Never click a link in an email without being absolutely sure you recognize the sender and the website destination. Remember, anchor text is not always reflective of the link destination.
- Call the company or email a familiar address if you’re unsure. When in doubt, reach out. Never reply to a suspicious email but call the customer service number from the company’s website (not from the email) and verify what email communications they may have sent recently. You can also screenshot the suspicious email if you’re verifying accuracy via email communications or a ticketing system.
5. Avoid giving out personal information over the phone
Like email, phone calls can be a means through which scammers try to get a hold of your personal information.
The best guidance here is never to provide sensitive information to someone who has called you. Ask who they are and where they’re calling from and then call the company directly to check. Do not use any phone numbers provided by the caller.
6. Align with companies that prioritize cybersecurity.
Protecting your personal information and data is a responsibility you must share with any company you do business with.
The last decade has had its fair share of corporate data breach stories, many of which affect the clients and consumers in their wake. In fact, cyber-attacks on businesses were up 31% between 2020 and 2021.3
The solution here is not to pull all your data and finances from the institutions and live off-grid with your savings in cash. Instead, you can protect your interests simply by aligning with people and businesses who make your privacy their priority.
Here at North Star, confidentiality and data security are top concerns. Integrity is one of our core values, and we remain dedicated to your rights, privacy, and information protection.
In 2023, we aligned with Cetera Advisor Networks as our broker-dealer/RIA. This gives us access to provide even better service to our clients and reinforce customer information privacy. With Cetera, we invest in security systems to protect customer information, including physical, electronic, and procedural safeguards.
Likewise, we limit the collection and storage of personally identifiable information (PII) to that necessary for us to administer business and provide quality service, and any third-party vendor we work with must comply to our high standard of security and complete a rigorous vendor due diligence process.
North Star operates in a heavily regulated industry, so some of the more prominent rules and laws we are required to adhere to include the following (not an all-inclusive list):
- The SEC’s Regulation S-P
- FINRA Rule 3120
- The Securities Exchange Act of 1933
- The Gramm-Leach-Bliley Act
- Individual State Privacy Laws
- HIPAA
- Broker-Dealer and Firm Level written policies and procedures
The bottom line
Knowing your financial institution is a key element in remaining safe online. When you have a personal relationship with someone managing your financial life—from investments to retirement to insurance—you can spot bad actors more easily. Likewise, if you receive a questionable request or email, you have an ally to turn to with your concerns.
Financial professionals are more than just money managers. Many financial professionals consider themselves their client’s advocates and confidants first and foremost, and they want to be the first person you reach out to if you’re concerned about any facet of your financial health—data security included!
If you are concerned about activity on an investment account or an insurance policy, don’t hesitate to reach out to your financial professional.
Get more financial wellness tips in your inbox!
1Presse, A. F. P.- A. F. (2022, May 10). Global cost of cybercrime topped $6 trillion in 2021: Defence firm. Barron’s. Retrieved September 26, 2022, from https://www.barrons.com/news/global-cost-of-cybercrime-topped-6-trillion-in-2021-defence-firm-01652198407
2Cost of a data breach 2022. IBM. (n.d.). Retrieved October 10, 2022, from https://www.ibm.com/reports/data-breach
3Accenture. State of Cybersecurity Resilience 2021.
Securities offered through Cetera Advisor Networks LLC, member FINRA/SIPC. Advisory Services offered through Cetera Investment Advisers LLC, a registered investment adviser. Cetera is under separate ownership from any other named entity.